Cyber Security.
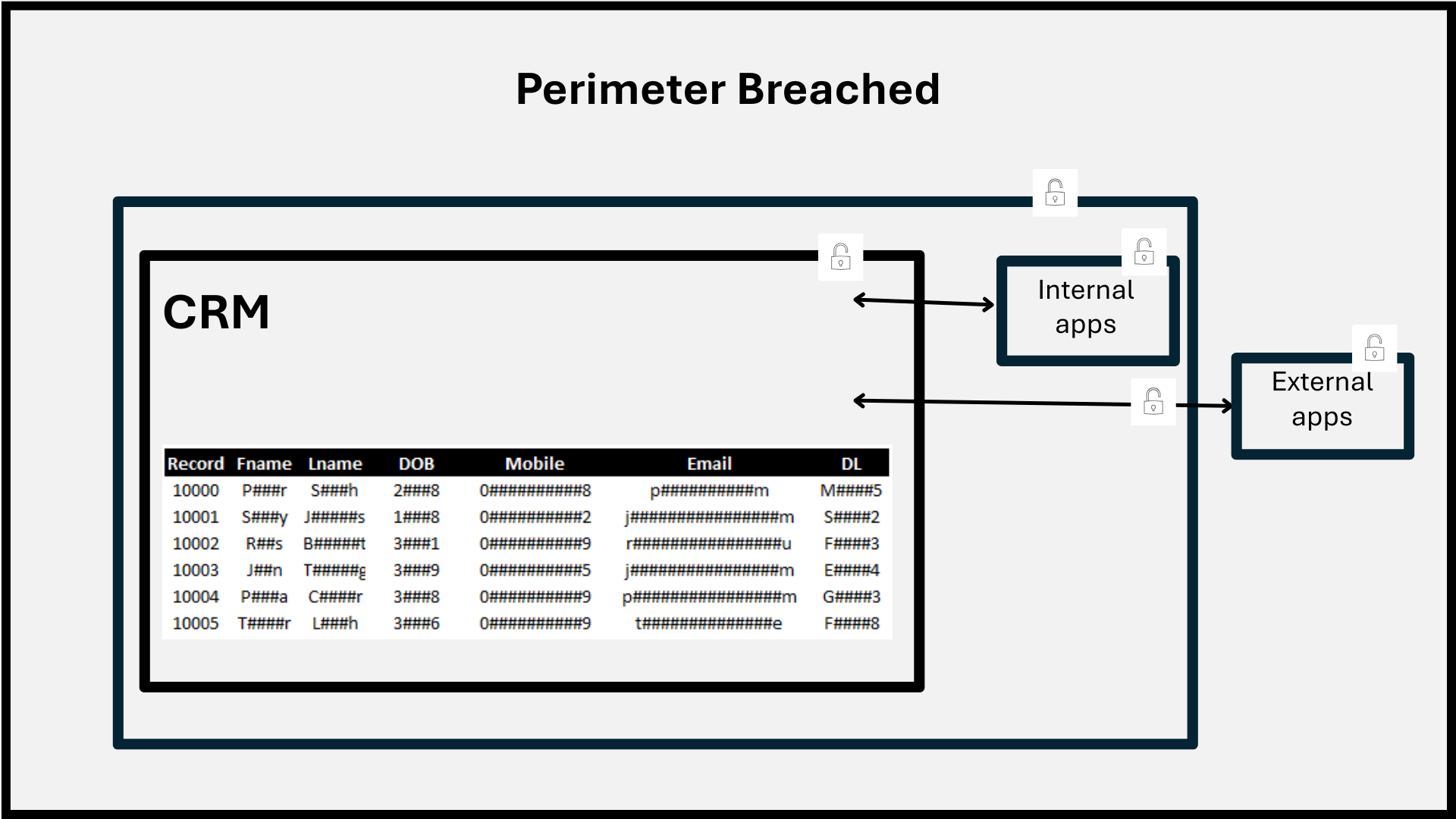
Everyone’s protecting the perimeter.
We’re protecting the data.
Most Cyber breaches access and release raw data.
We’re looking at this a little differently.
Perimeter enforcement remains critical.
Data encryption helps, but is sub-optimal.
Tokenisation provides next-level protection.
See TokenSecure™ in Action
What would we know?
Security and risk mitigation led
~20 years company experience in the advanced tokenization space
Architected for rapid deployment and scaleout
Earlier adopters of security-centric industry accreditations
Consultative at core
Contact us for a discussion
Discussions will be subject to execution of our NDA.